这篇博客是我根据wp自己复现的博客,建议大家还是看官方wp,这篇博客也是学习
借鉴博客
[原创]脚本类恶意程序分析技巧汇总-软件逆向-看雪-安全社区|安全招聘|kanxue.com
H&NCTF 2024 官方WP (qq.com)
VBS病毒是用VB Script编写的,它利用Windows系统的开放性,一般window本地就有
解这道题,我们先打开vs
随便打开一个项目
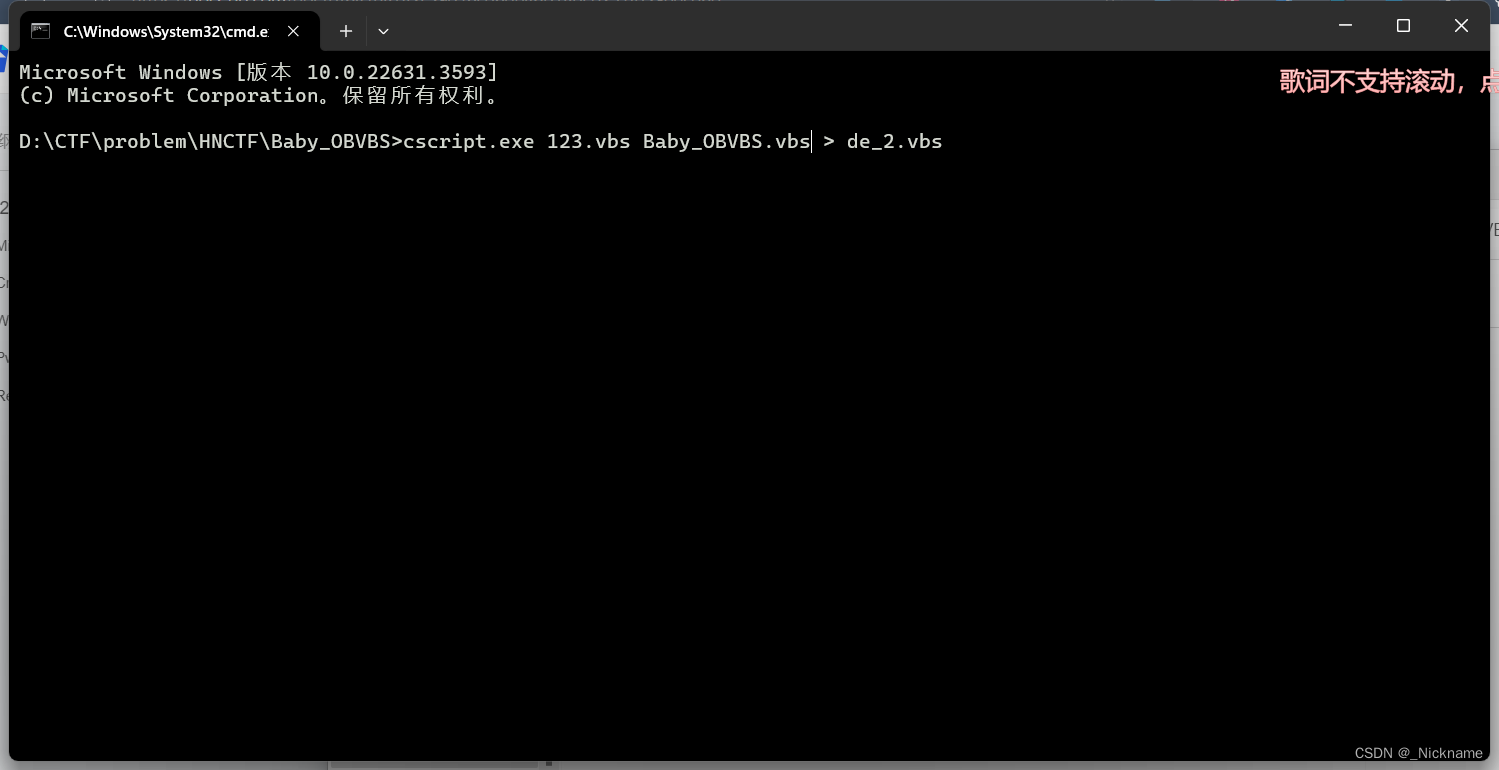
win+r打开命令行
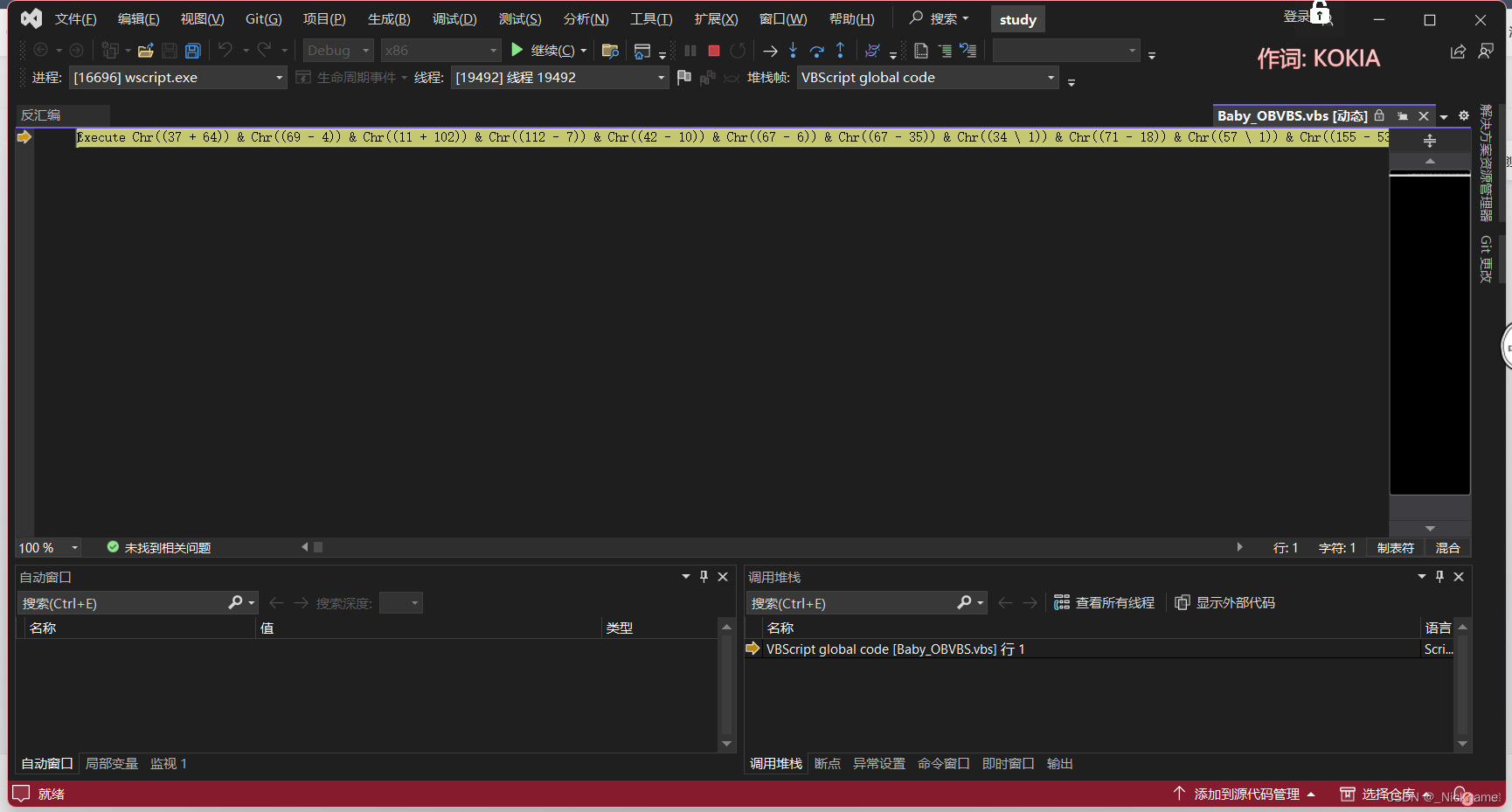
输入 wscript /X "D:\CTF\problem\HNCTF\Baby_OBVBS\Baby_OBVBS.vbs"
或者cscript.exe /x"D:\CTF\problem\HNCTF\Baby_OBVBS\Baby_OBVBS.vbs"
直接确定
如果没有显示代码,换一个命令 外加 多试几次
太多了,我尝试,我代码能力比较差,写不出来自动脚本
这里我就直接抄WP的代码了
Option Explicit
Function Defuscator(vbs)
Dim t
t = InStr(1, vbs, "Execute", 1)
t = Mid(vbs, t + Len("Execute"))
t = Eval(t)
Defuscator = t
End Function
Dim fso, i
Const ForReading = 1
Set fso = CreateObject("Scripting.FileSystemObject")
For i = 0 To WScript.Arguments.Count - 1
Dim FileName
FileName = WScript.Arguments(i)
Dim MyFile
Set MyFile = fso.OpenTextFile(FileName, ForReading)
Dim vbs
vbs = MyFile.ReadAll
WScript.Echo Defuscator(vbs)
MyFile.Close
Next
Set fso = Nothing
这段VBScript代码定义了一个名为Defuscator的函数,其主要功能是读取并执行来自其他VBScript文件中的特定代码段。下面是对整个脚本的详细解释:
Option Explicit: 这一行声明要求在使用变量之前必须显式声明它们,以避免因拼写错误或未初始化的变量而引起的错误。
Defuscator Function: 定义了一个名为Defuscator的函数,它接受一个参数vbs(预期是一个包含VBScript代码的字符串)。
- 使用InStr(1, vbs, "Execute", 1)查找"Execute"第一次出现的位置。这通常用于定位嵌入在输入字符串中的特定命令或模式。
- Mid(vbs, t + Len("Execute"))从"Execute"之后的字符开始截取字符串,假设之后的内容是要执行的VBScript代码。
- Eval(t)函数会计算并执行截取出的字符串t作为VBScript代码。这是一种动态执行代码的方式,非常灵活但也可能引入安全风险。
- 最后,Defuscator函数返回执行结果。
文件操作部分:
- 通过Dim fso, i声明了两个变量,fso用于文件系统操作,i用于循环计数。
- Const ForReading = 1定义了一个常量,表示以只读模式打开文件。
- 使用CreateObject("Scripting.FileSystemObject")创建一个FileSystemObject实例,允许进行文件和目录操作。
- 通过WScript.Arguments.Count遍历命令行传入的所有参数(这些参数应该是文件名)。
- 对于每个参数(即每个文件名),打开文件,读取所有内容到变量vbs中。
- 调用Defuscator(vbs)函数来执行读取到的VBScript代码,并通过WScript.Echo输出执行结果。
- 读取完成后关闭文件。
清理: Set fso = Nothing释放对FileSystemObject实例的引用,这是良好编程习惯,有助于及时释放资源。
总结来说,这段脚本设计用于读取一系列指定的VBScript文件,寻找并执行其中以"Execute"关键字开始的代码段,然后打印出执行结果。这种类型的脚本可能用于处理或分析已编码或混淆的VBScript代码,但同时也需要注意,直接执行未经检查的代码存在安全隐患
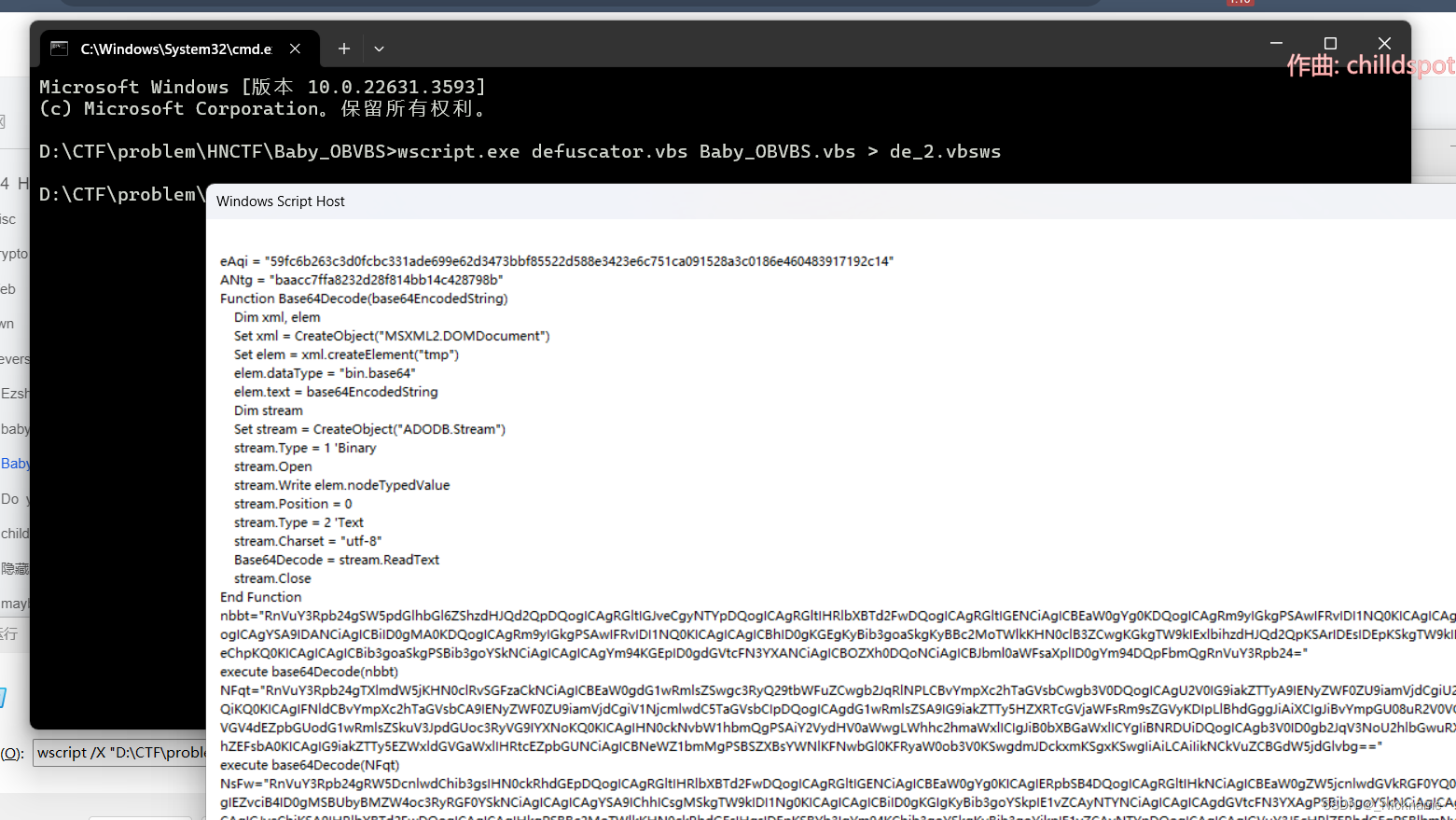
将上面的脚步,保存一下
cscript.exe defuscator.vbs Baby_OBVBS.vbs > de_2.vbs
我的cscript有问题
我用是ws
wscript.exe defuscator.vbs Baby_OBVBS.vbs > de_2.vbs
Function Defuscator(vbs)
Dim t
t = InStr(1, vbs, "Execute", 1)
t = Mid(vbs, t + Len("Execute"))
t = Eval(t)
Defuscator = t
End Function
Dim fso, i, outFile
Const ForReading = 1, ForWriting = 2
Set fso = CreateObject("Scripting.FileSystemObject")
' 创建或打开一个文件用于写入输出
Set outFile = fso.OpenTextFile("output.txt", ForWriting, True)
For i = 0 To WScript.Arguments.Count - 1
Dim FileName
FileName = WScript.Arguments(i)
Dim MyFile
Set MyFile = fso.OpenTextFile(FileName, ForReading)
Dim vbs
vbs = MyFile.ReadAll
outFile.WriteLine Defuscator(vbs)
MyFile.Close
Next
outFile.Close
Set fso = Nothing
这是我自己改的代码,直接的那个弹窗很不方便,我就文件读写进了txt文档,方便阅读
命令是一样的
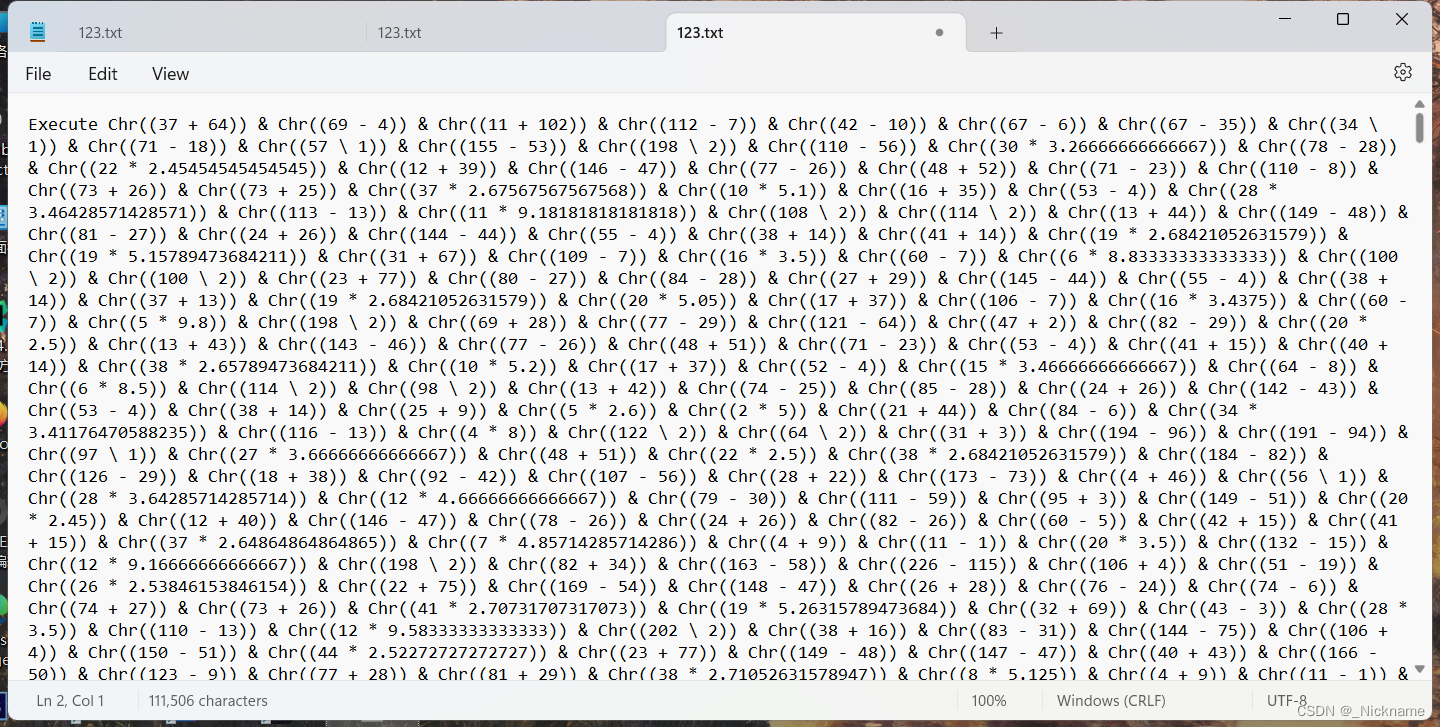
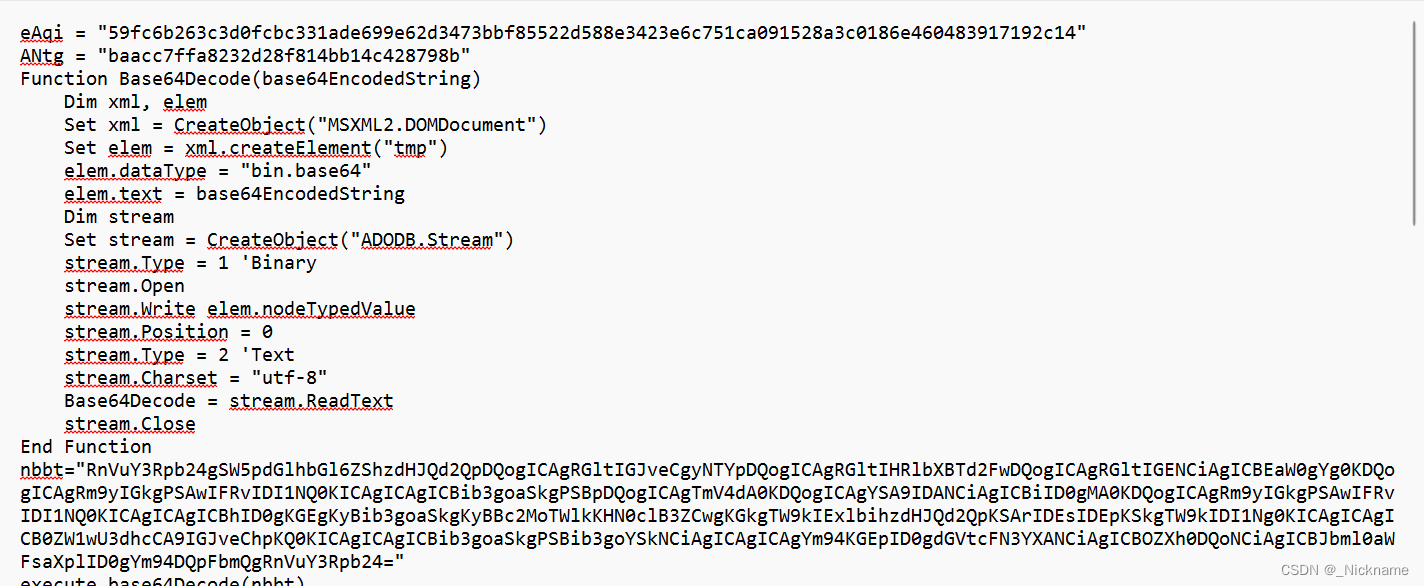
就得到了这个
每段base之后就是一段代码
再保存下
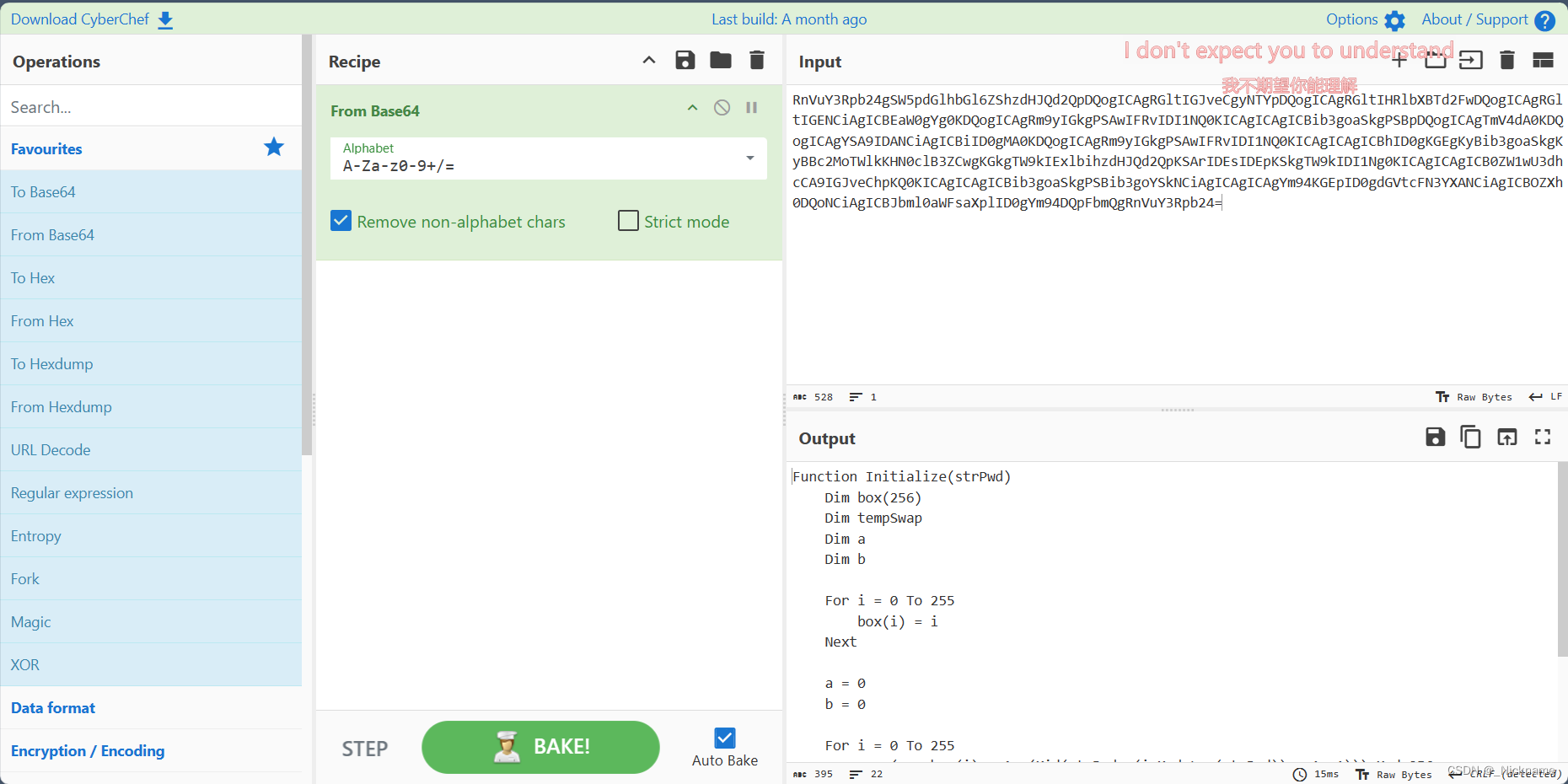
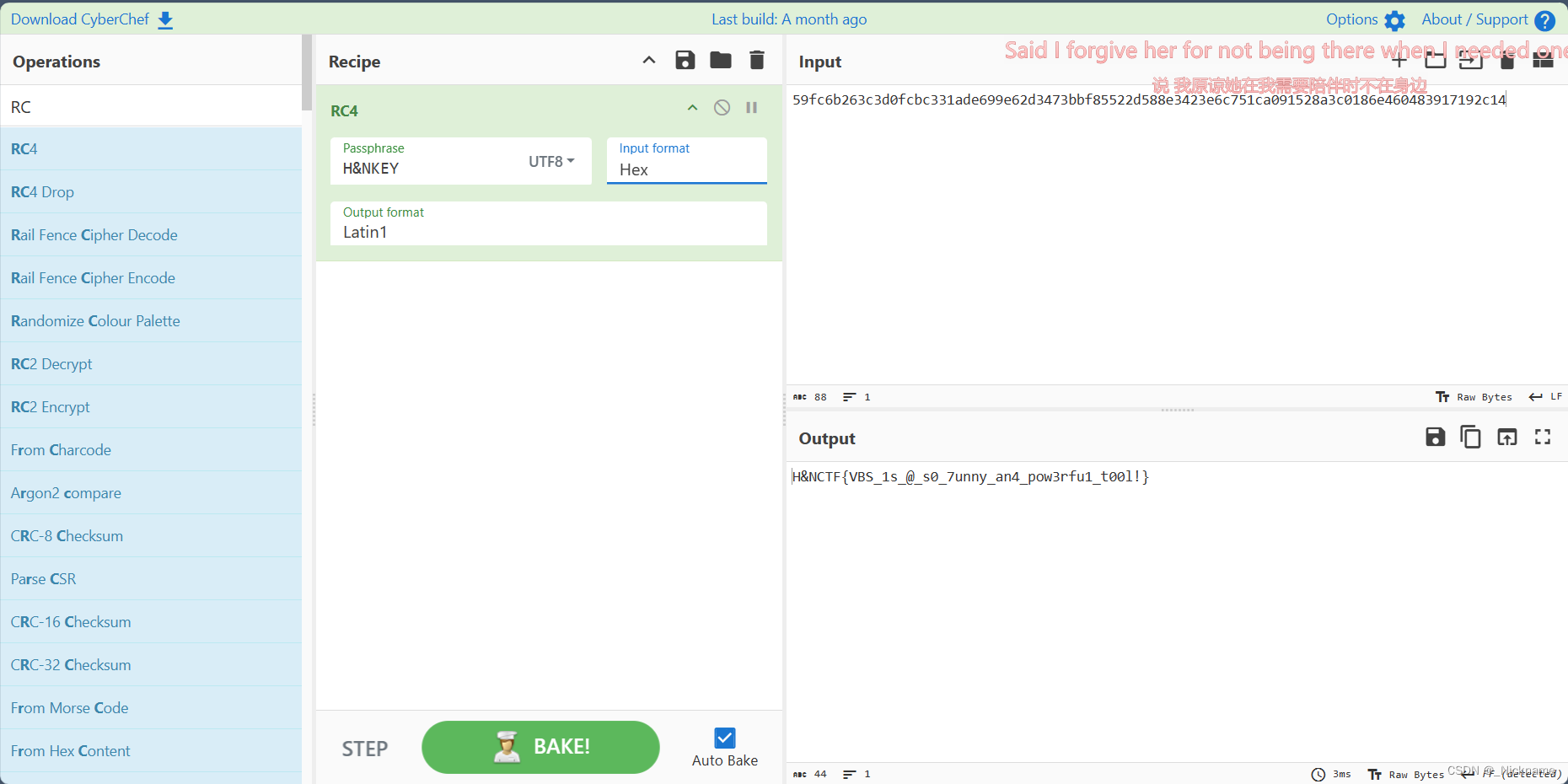
eAqi = "59fc6b263c3d0fcbc331ade699e62d3473bbf85522d588e3423e6c751ca091528a3c0186e460483917192c14"
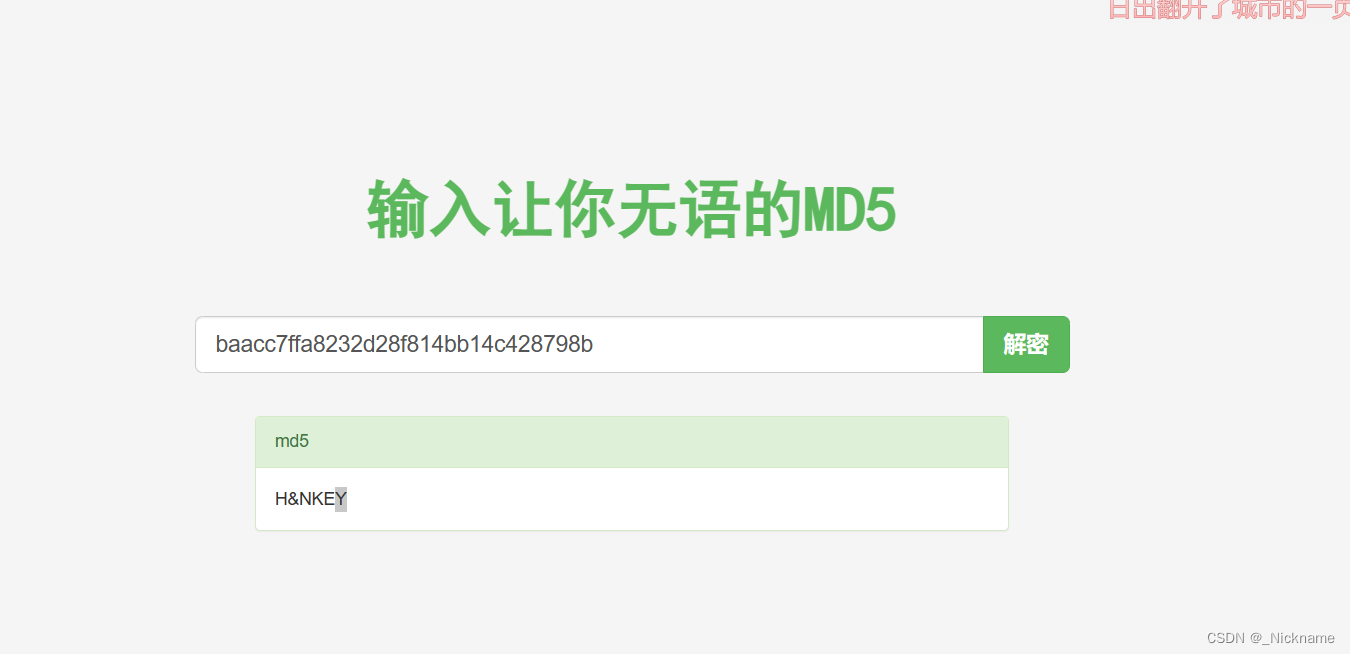
ANtg = "baacc7ffa8232d28f814bb14c428798b"
Function Initialize(strPwd)
Dim box(256)
Dim tempSwap
Dim a
Dim b
For i = 0 To 255
box(i) = i
Next
a = 0
b = 0
For i = 0 To 255
a = (a + box(i) + Asc(Mid(strPwd, (i Mod Len(strPwd)) + 1, 1))) Mod 256
tempSwap = box(i)
box(i) = box(a)
box(a) = tempSwap
Next
Initialize = box
End Function
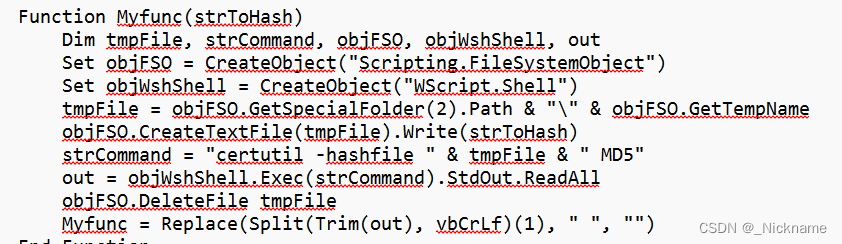
Function Myfunc(strToHash)
Dim tmpFile, strCommand, objFSO, objWshShell, out
Set objFSO = CreateObject("Scripting.FileSystemObject")
Set objWshShell = CreateObject("WScript.Shell")
tmpFile = objFSO.GetSpecialFolder(2).Path & "\" & objFSO.GetTempName
objFSO.CreateTextFile(tmpFile).Write(strToHash)
strCommand = "certutil -hashfile " & tmpFile & " MD5"
out = objWshShell.Exec(strCommand).StdOut.ReadAll
objFSO.DeleteFile tmpFile
Myfunc = Replace(Split(Trim(out), vbCrLf)(1), " ", "")
End Function
Function EnCrypt(box, strData)
Dim tempSwap
Dim a
Dim b
Dim x
Dim y
Dim encryptedData
encryptedData = ""
For x = 1 To Len(strData)
a = (a + 1) Mod 256
b = (b + box(a)) Mod 256
tempSwap = box(a)
box(a) = box(b)
box(b) = tempSwap
y = Asc(Mid(strData, x, 1)) Xor box((box(a) + box(b)) Mod 256)
encryptedData = encryptedData & LCase(Right("0" & Hex(y), 2))
Next
EnCrypt = encryptedData
End Function
msgbox "Do you know VBScript?"
msgbox "VBScript (""Microsoft Visual Basic Scripting Edition"") is a deprecated Active Scripting language developed by Microsoft that is modeled on Visual Basic."
msgbox "It allows Microsoft Windows system administrators to generate powerful tools for managing computers without error handling and with subroutines and other advanced programming constructs. It can give the user complete control over many aspects of their computing environment."
msgbox "Interestingly, although VBScript has long since been deprecated, you can still run VBScript scripts on the latest versions of Windows 11 systems."
msgbox "A VBScript script must be executed within a host environment, of which there are several provided with Microsoft Windows, including: Windows Script Host (WSH), Internet Explorer (IE), and Internet Information Services (IIS)."
msgbox "For .vbs files, the host is Windows Script Host (WSH), aka wscript.exe/cscript.exe program in your system."
msgbox "If you can not stop a VBScript from running (e.g. a dead loop), go to the task manager and kill wscript.exe/cscript.exe."
msgbox "cscript and wscript are executables for the scripting host that are used to run the scripts. cscript and wscript are both interpreters to run VBScript (and other scripting languages like JScript) on the Windows platform."
msgbox "cscript is for console applications and wscript is for Windows applications. It has something to do with STDIN, STDOUT and STDERR."
msgbox "OK! Now, let us begin our journey."
key = InputBox("Enter the key:", "CTF Challenge")
if (key = False) then wscript.quit
if (len(key)<>6) then
wscript.echo "wrong key length!"
wscript.quit
end if
If (Myfunc(key) = ANtg) Then
wscript.echo "You get the key!Move to next challenge."
Else
wscript.echo "Wrong key!Try again!"
wscript.quit
End If
userInput = InputBox("Enter the flag:", "CTF Challenge")
if (userInput = False) then wscript.quit
if (len(userInput)<>44) then
wscript.echo "wrong!"
wscript.quit
end if
box = Initialize(key)
encryptedInput = EnCrypt(box, userInput)
If (encryptedInput = eAqi) Then
MsgBox "Congratulations! You have learned VBS!"
Else
MsgBox "Wrong flag. Try again."
End If
wscript.echo "bye!"
最后就是这样一段
myfun就是md5
MD5免费在线解密破解_MD5在线加密-SOMD5
又学到一个东西



![[工业自动化-1]:PLC架构与工作原理](https://img-blog.csdnimg.cn/ce10a1471ed14382bc58364cf8bd5209.png)



还没有评论,来说两句吧...